
Perisai - Cybersecurity
🌐 Trusted by all sizes of organizations
💻 Hyperautomated modular cybersecurity with AI-driven
🛡️ #YouBuildWeGuard #HackersAssembled
⬇️ Sign up now!
Recent Posts

Exciting news: Peris.ai is selected for the Huawei Cloud Startup Ignite Competition FINAL 2023! Formerly known as Spark Ignite, it has become one of Asia's premier startup competitions. 🗓️ Save the Date for the Final Pitch Day: October 17th, 2023, from 9:30 am to 1:30 pm. 🏙 Location: Sky100, Kowloon - an iconic spot in Hong Kong. Don’t miss this amazing event, especially for updates on Peris.ai Cybersecurity. Secure your spot now and witness the future of startups as it unfolds before your eyes! https://lnkd.in/guQmW45P #Perisai #Cybersecurity #YouBuild #WeGuard #HuaweiCloud #StartupIgnite #TechInnovation #CloudTechnology #TechStartup #2023Innovations #TechCompetition #Startup #Asia

🚀 Exciting news from Peris.ai! We are honored to be part of the TOP100 Growth Program 2024, alongside a dynamic group of startups poised to transform the SEA startup ecosystem. From automation to AI-driven threat detection, we're here to secure your digital world. #TOP100 #StartupGrowth #CybersecurityInnovation #SEAEcosystem #DigitalSecurity #AIThreatDetection #Innovation #Perisai #Cybersecurity #YouBuild #WeGuard

🏆 We are proud to be named the Regional Winner for People's Choice of the Year and the Regional Winner for Best Newcomer of the Year. These accolades are a testament to our commitment to innovation and excellence in cybersecurity. Find more about this edition and the list of all winners here https://aseanstartupawards.com/edition10/?utm_content=190014681&utm_medium=social&utm_source=linkedin&hss_channel=lcp-17908463 Secure Global, Global Secure! #ASEANStartupAwards #Perisai #Cybersecurity #YouBuild #WeGuard

🚨 Could Your Password Be the Reason Hackers Get In? Brute force attacks are on the rise, and weak passwords are their biggest allies. Hackers use advanced tools and automation to guess their way into sensitive systems, leaving your data and business at risk. Think "1234" is secure? Think again. #CyberSecurityTips #BruteForceAttack #PasswordProtection #DataSecurity #CyberThreats #CyberHygiene #InfoSec #StaySecure
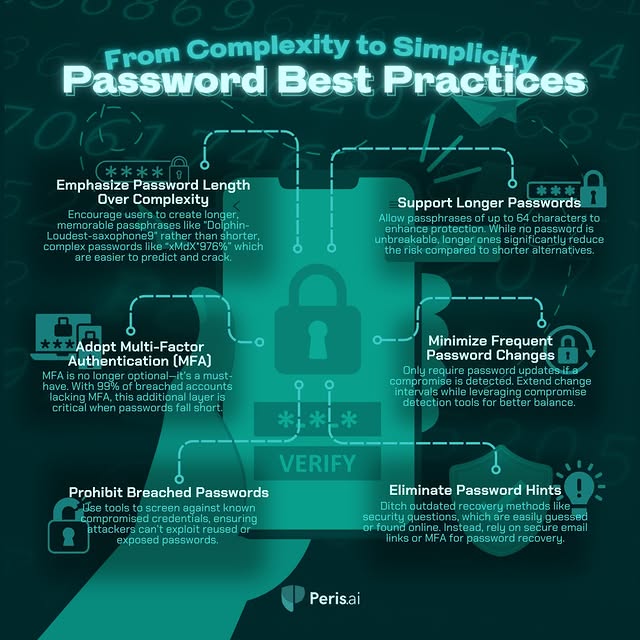
Are your passwords truly secure, or just complicated? Learn how to prioritize length over complexity, implement MFA, and avoid common pitfalls like mandatory changes and weak hints. Password security doesn't have to be hard – it just has to be smart. 💡 Pro tip: A password like 'llama-shoehorn-trumpet7' is both memorable and tough to crack. Ready to upgrade your strategy?" #PasswordSecurity #CybersecurityTips #MFA #DataProtection #DigitalSafety #StrongPasswords #CyberResilience #ITBestPractices #Perisai #Cybersecurity #YouBuild #WeGuard

Looking to break into cybersecurity? 🛡️ These are the top skills employers can’t ignore in 2024. Do you have what it takes? 🚀 #HiringTrends #TechSkills #CloudSecurity #RiskManagement #ApplicationSecurity #AIinCybersecurity #CareerGrowth #PerisAI #Cybersecurity #YouBuild #WeGuard

Why Are Cyber Threats Exploding? 🚨 From insider risks to IoT vulnerabilities, here are 10 shocking reasons your business might be the next target. Are you prepared to fight back? #DataProtection #CyberThreats #IoTSecurity #InsiderThreats #TechLeadership #SupplyChainSecurity #CyberAwareness #PerisAI #Cybersecurity #YouBuild #WeGuard
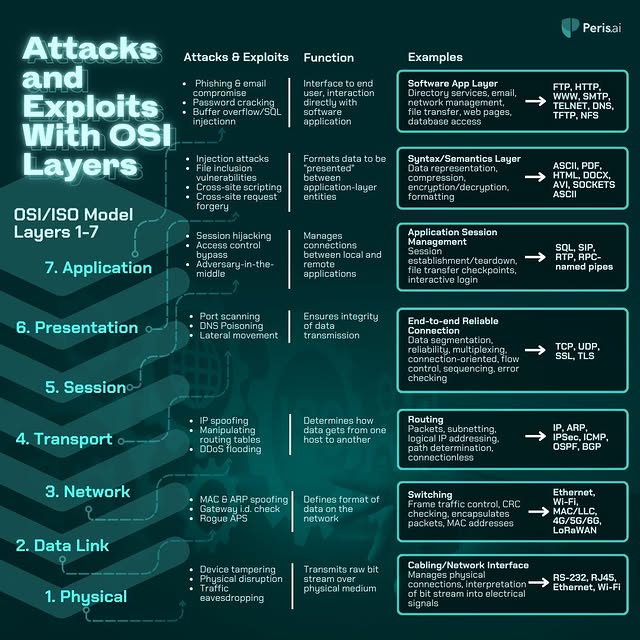
🌐 Unpacking OSI Layers: How Cyber Attacks Exploit Each Level! 🛡️ The OSI Model isn’t just for IT professionals—it’s a blueprint for understanding how cyber attacks target each layer of a network. Cybercriminals know where vulnerabilities lie, and they exploit everything from the physical connection to your web applications. Let’s break it down layer by layer: - Application Layer (Layer 7): The most visible attack layer! Think phishing emails, SQL injection, and password cracking targeting your apps directly. - Presentation Layer (Layer 6): Vulnerabilities like file inclusion and cross-site scripting sneak into how data is formatted or presented. - Session Layer (Layer 5): Session hijacking and adversary-in-the-middle attacks compromise active connections between users and apps. - Transport Layer (Layer 4): DDoS attacks and rogue data manipulation target your data flow and reliability. - Network Layer (Layer 3): IP spoofing and routing manipulation focus on how packets travel between hosts. - Data Link Layer (Layer 2): MAC spoofing and rogue access points exploit local network setups. - Physical Layer (Layer 1): The foundation of all attacks—think tampering with cables or hardware to intercept sensitive data. 🛠️ Why it Matters: Understanding the OSI model helps IT teams proactively secure each layer, ensuring end-to-end network protection. Learn how attackers operate and what tools can help you fortify your defenses! #CyberSecurity #OSIModel #ThreatProtection #NetworkDefense #DigitalSecurity #PenetrationTesting #DataSafety #CyberThreats

Protect Yourself From The Common Cyber Attack Tactics You Need to Know! Are You Prepared? 🚨 #CyberSecurityAwareness #PhishingScams #DigitalSafety #RansomwareProtection #StaySafeOnline #CyberThreats #ProtectYourData #InfosecTips #PerisAI #Cybersecurity #YouBuild #WeGuard

🔒 Striking the right balance in cybersecurity is essential. Acknowledging risks without being overwhelmed by them ensures a proactive, focused, and resilient approach to digital defense. #CybersecurityAwareness #RiskManagement #CyberResilience #StephaneNappoQuotes #DigitalDefense #CyberThreats #InformationSecurity #ProactiveProtection #PerisAI #Cybersecurity #YouBuild #WeGuard

Must-Read Cybersecurity Books to Gift (or Keep) This Holiday From uncovering hacker tactics to building AI security, these must-read books are perfect for gifting—or keeping! Whether you're a seasoned professional or just starting in cybersecurity, there's something here to inspire and educate. 📖 What's on your reading list this holiday? #CybersecurityBooks #OnlineSafety #EthicalHacking #TechLearning #AIandSecurity #CyberRiskManagement #CyberThreats #DigitalPrivacy #PerisAI #Cybersecurity #YouBuild #WeGuard

Peris.ai is honored to have been invited by the Directorate General of IKMA, Ministry of Industry-RI [ @kemenperin_ri ], to showcase our cybersecurity solutions at Manufacturing Indonesia 2024, held from December 4-7 at Jakarta International Expo, Kemayoran. This premier event, celebrating 35 years of innovation, brought together over 1,300 exhibitors from 32 countries, highlighting the latest advancements in the manufacturing sector. Our participation underscores our commitment to enhancing cybersecurity within Indonesia's manufacturing industry, aligning with the nation's goals for digital transformation and industrial resilience. #ManufacturingIndonesia2024 #DigitalTransformation #Industry40 #CyberDefense #IndonesiaIndustry #TechInnovation #PerisaiAtMFI2024 #PerisAI #Cybersecurity #YouBuild #WeGuard
Similar Influencers

News Cuff

Program Coding

El Rincón de China

Discover.Indo

KABUPATEN BANDUNG BARAT BERKABAR

Kreatif Videografer | Visual Story Maker

Info Lomba Indonesia

Kompas Tekno

TIMES Indonesia

Merdeka Siber • Belajar Cyber Security Dari Nol!

Vritimes Singapore

Pt. Visindo Prima Nusantara

Google Developer Group on Campus ITS

Bawana Margatama| Tips & Loker

#TransformTogether - Appkuni

Jaya Media Computer

InvestIdea Tech Showcase Day

The Leap - Insights | Podcasts | GTM

Genz.id

Ngonsul IT

IEAE - International Electronics and Smart Appliance Expo

Petani Kode | Coding & Growing

THOTH AI

Tips dan Trik Mahasiswa

TECNO Indonesia

DroidLime

officialinews

Dari Kamar | Creator Lynk

carikill | upgrade skill digital
